Web Sec Challenges
Day 16 Flag:
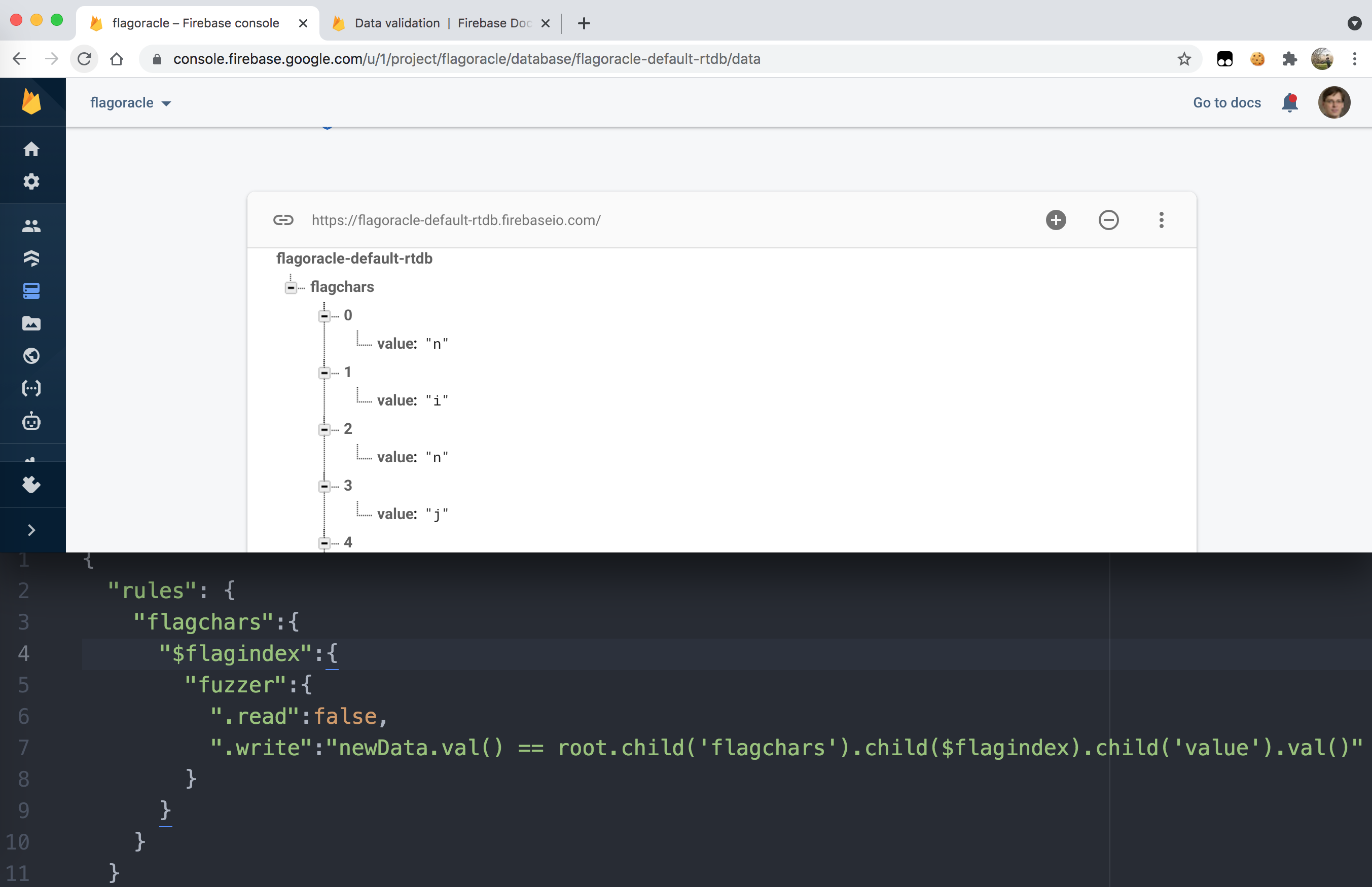
(Network Monitoring) Day 25: sniffer101
(OTP xor)Day 26: OTP
(10 flags RSA workshop): Day 27+28+29: RSA workshop in a box
Day 30: Flag then reverse shell at https://general-fish-ssti.onrender.com/stuffhere and Source code here
Day 31: LSB stego matrix.png

Day 32: WASM Reverse https://websec.prof.ninja/ctf/wasmrev/